The top little bit from the byte (also the major bit in the very first nibble) is flipped to make 00000111, which happens to be 0x07, as revealed within the lessen sample.
Spread the loveWhen turning into a leader in the sphere of training, it is important to consider equity. Some learners may not have use of devices or the net from their ...
Vulnerability to Advanced Threats: The possibilities of brute-pressure assaults, collision assaults, and other cryptographic attacks grow to be better as computational power raises. MD5’s flaws ensure it is In particular liable to these threats, compromising security.
This characteristic, generally known as the 'avalanche outcome', enhances the algorithm's sensitivity to knowledge modifications. So, when you are sending your song lyrics and in some cases a person word adjustments in transit, MD5 will capture it!
Initially off, the MD5 algorithm will take your enter—as an instance it's the text of your favorite track—and splits it into blocks of 512 bits each.
Confined Digital Signatures: When protection was not the leading priority, MD5 algorithms produced electronic signatures. Even so, because of its vulnerability to collision attacks, it is actually unsuited for robust electronic signature purposes.
MD5 is also used in digital signatures. Much like how a Bodily signature verifies the authenticity of a document, a digital signature verifies the authenticity of digital knowledge.
MD3 is yet another hash functionality intended by Ron Rivest. It had several flaws and never seriously created it out from the laboratory…
While in the context of MD5, a 'salt' is yet another random benefit that you include to the facts right before hashing. This causes it to be much tougher for an attacker to guess your info based upon the hash.
A single-way compression capabilities can’t cope with variable inputs, so MD5 gets around this by padding out its facts, to make certain that it is often processed in 512-little bit blocks of data.
1st off, MD5 is rapid and efficient. It really is similar to the hare in the race towards the tortoise—it will get The task finished quickly. This speed can be a important variable when you're processing big amounts of knowledge.
The first info can not be check here retrieved or reconstructed through the hash. It's like turning your letter into that exclusive seal—we know it's your letter, but we won't read it!
// Initialize hash benefit for this chunk: var int A := a0 var int B := b0 var int C := c0 var int D := d0
By distributing this type, I realize and acknowledge my information will probably be processed in accordance with Progress' Privateness Plan.
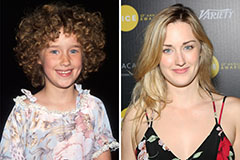 Ashley Johnson Then & Now!
Ashley Johnson Then & Now!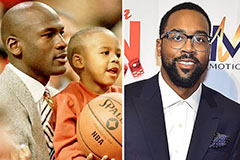 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Tonya Harding Then & Now!
Tonya Harding Then & Now! Mike Smith Then & Now!
Mike Smith Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!